- Topic1/3
58 Popularity
22k Popularity
4k Popularity
4k Popularity
170k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is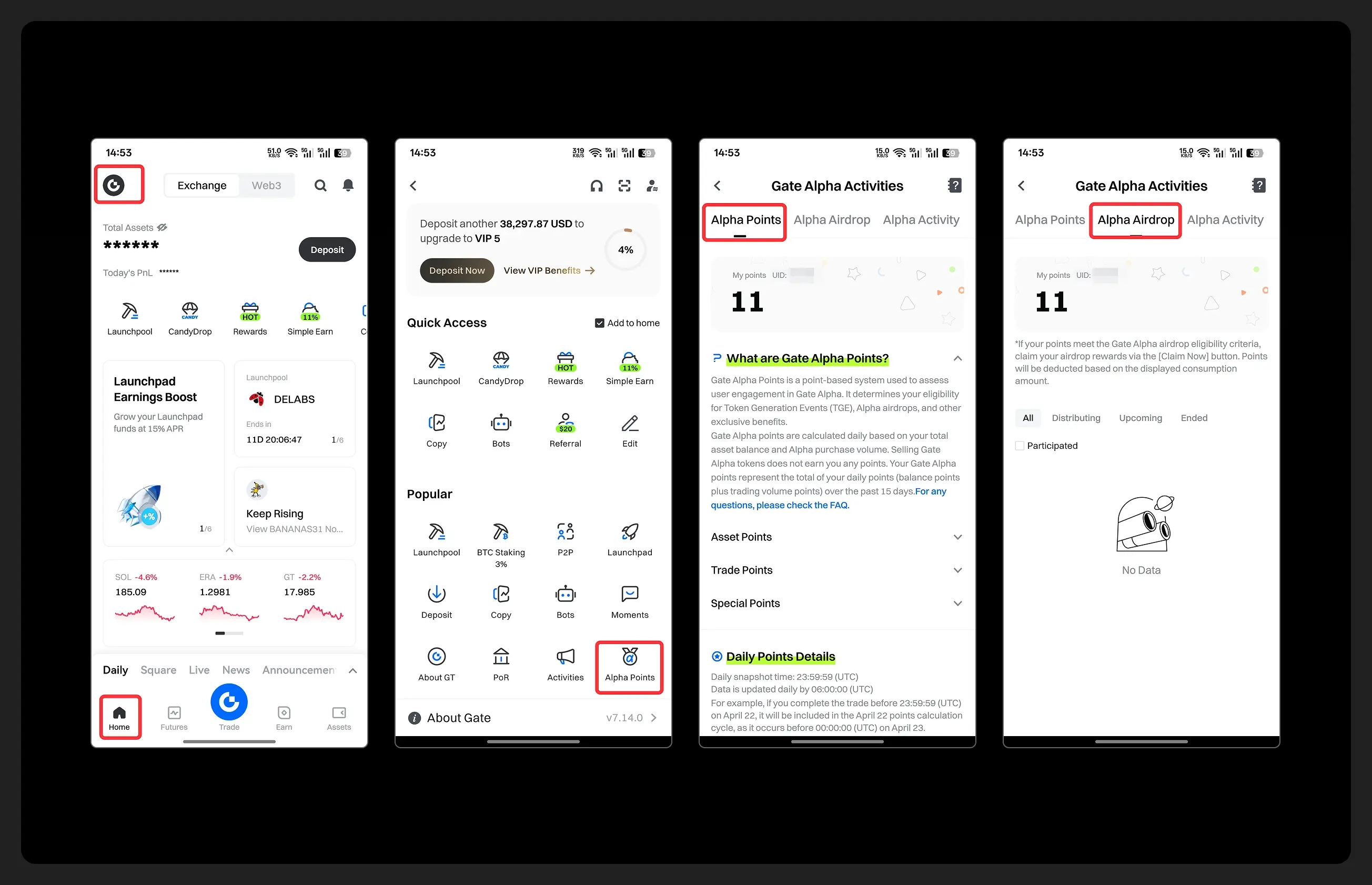
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
FHE, ZK, and MPC: A Comparative Analysis of Three Major Privacy Protection Technologies
Comparative Analysis of FHE, ZK, and MPC Cryptography Techniques
In the field of Cryptography, Fully Homomorphic Encryption ( FHE ), Zero-Knowledge Proof ( ZK ), and Multi-Party Computation ( MPC ) are three important privacy protection technologies. Although they all aim to protect data privacy and security, there are some differences in specific application scenarios and technical characteristics. This article will provide a detailed comparison of these three technologies.
Zero-Knowledge Proof ( ZK )
Zero-knowledge proof technology focuses on how to verify the truth of a statement without revealing any specific information. It is based on Cryptography and allows one party, the prover, to prove to another party, the verifier, that they know a certain secret without disclosing any information about that secret.
For example, Alice can prove her good credit to the car rental company employee Bob without having to show specific bank statements. The "credit score" of payment software is similar to a type of zero-knowledge proof, which can demonstrate a user's credit status without revealing specific transaction records.
In the blockchain field, anonymous coins are a typical application of ZK technology. When users make transfers, they need to prove their transfer authority while maintaining anonymity. By generating ZK proofs, miners can verify the legitimacy of transactions and put them on the chain without knowing the identity of the transactors.
Multi-Party Computation ( MPC )
Multi-party secure computation technology mainly addresses how to allow multiple participants to jointly complete computational tasks without disclosing sensitive information from each party. It enables multiple parties to collaborate on computations without revealing their respective input data.
A classic application scenario of MPC is: Alice, Bob, and Carol want to calculate the average salary of the three of them, but do not want to disclose the specific salary amounts to each other. Through MPC technology, they can divide their respective salaries into three parts, exchange two parts with each other, and then sum the received numbers and share the result. Finally, the three of them sum the three results again and average them, which will give them the average salary, but they will not know each other's specific salary amounts.
In the cryptocurrency field, MPC wallets are an important application. They divide the private key into multiple parts, which are jointly held by users, the cloud, and exchanges, enhancing the security of assets. Even if a user loses their phone, they can recover the private key through other parties. Some MPC wallets also support the introduction of more third parties to further enhance security.
Fully Homomorphic Encryption ( FHE )
Homomorphic encryption technology focuses on how to encrypt data so that the encrypted data can be given to untrusted third parties for computation, while the computation results can still be correctly decrypted. This enables the use of external computing resources while protecting data privacy.
A typical application scenario of FHE is: Alice does not have sufficient computational power and needs to rely on Bob for calculations, but she does not want to disclose the real data to Bob. Through FHE, Alice can encrypt the original data and then let Bob process the encrypted data. Finally, Alice can decrypt it to obtain the real result, while Bob cannot know the content of the original data throughout the entire process.
In the blockchain field, FHE can be used to solve some problems in PoS consensus mechanisms. For example, in some small PoS networks, nodes may tend to directly follow the verification results of large nodes rather than verifying themselves, which can lead to centralization issues. Through FHE technology, nodes can complete block verification without knowing the answers of other nodes, avoiding mutual plagiarism.
In addition, FHE can also be applied to scenarios such as decentralized voting to prevent voters from influencing each other. Some projects are exploring the combination of FHE with re-staking ( to provide more secure outsourced node services for small blockchains.
![FHE vs ZK vs MPC, what are the differences between the three encryption technologies?])https://img-cdn.gateio.im/webp-social/moments-0b3f906bfa44f66a733257e13cbb05af.webp(
Technical Comparison
Although these three technologies are all dedicated to protecting data privacy and security, there are some differences in their application scenarios and technical complexity:
Application Scenarios:
Technical Complexity:
![What are the differences between FHE, ZK, and MPC, three encryption technologies?])https://img-cdn.gateio.im/webp-social/moments-33f55404ecc37f43e873e59e4b19a361.webp(
Conclusion
With the development of the digital age, data security and personal privacy protection face unprecedented challenges. FHE, ZK, and MPC are three cryptography technologies that provide us with powerful privacy protection tools, each playing an important role in different scenarios. Understanding the characteristics and application scenarios of these technologies is crucial for building a safer and more private digital world.
![What are the differences between FHE, ZK, and MPC, three cryptographic technologies?])https://img-cdn.gateio.im/webp-social/moments-a8afc06a0d1893b261415caa9cd92e6a.webp(